Tails for Anarchists
 Published on
| Last edited on
Published on
| Last edited on
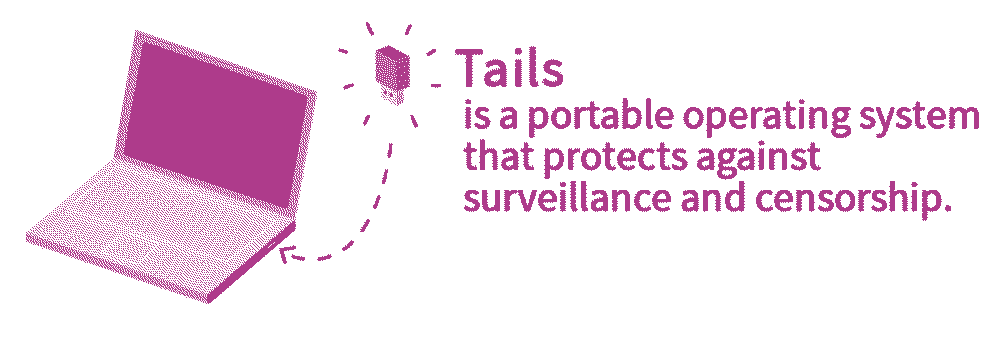
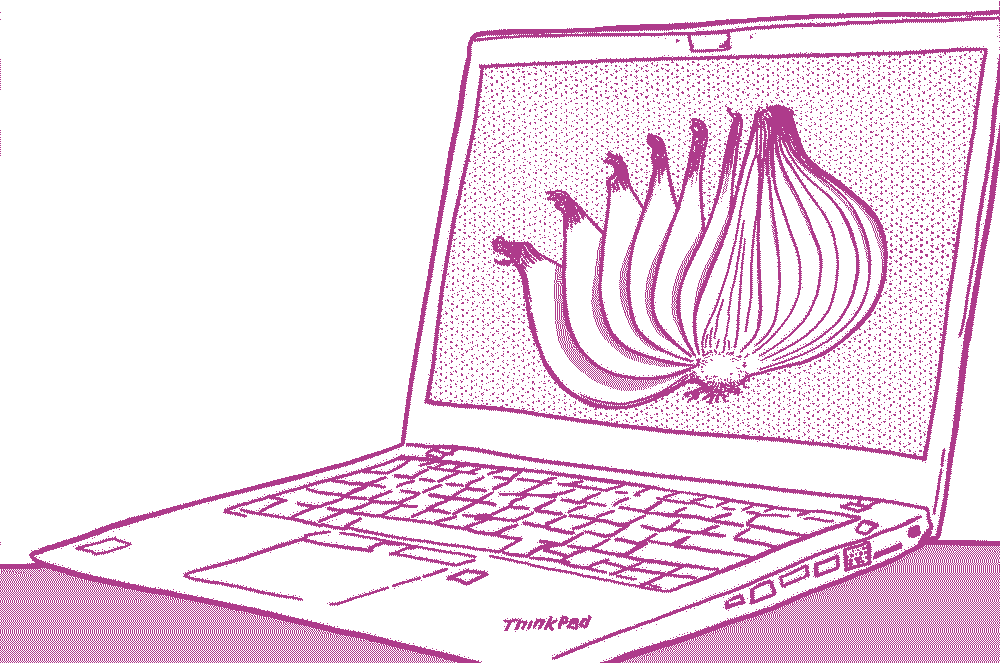
Tails is an operating system that makes anonymous computer use accessible to everyone. Tails is designed to leave no trace of your activity on your computer unless you explicitly configure it to save specific data. It accomplishes this by running from a DVD or USB, independent of the operating system installed on the computer. Tails comes with several built-in applications preconfigured with security in mind, and all anarchists should know how to use it for secure communication, research, editing, and publishing sensitive content.
Read More